Cybercriminals are incredibly adaptable. They learn new security measures quickly and find new ways to steal sensitive information.
One of the most common techniques used to exploit web users is the phishing scam. This article will cover what phishing is, cybercriminals’ different approaches, and how to prevent yourself from becoming a victim.
What is Phishing?
Phishing is a type of social engineering scam most commonly hidden in a fraudulent email but sometimes via text message, website, or phone call where a criminal posing as a legitimate institution, such as a bank or service, tries to obtain sensitive information from a target victim.
If the victim ‘takes the bait,’ the criminal will use malicious links, attachments, or simple instructions to obtain sensitive information such as:
- Usernames
- Passwords
- Social Security Number
- Address
- Credit card numbers
- Any personally identifiable information
History of Phishing
The term “phishing” came about in the mid- 1990s when a group of hackers posed as AOL employees using instant messenger and emails to “fish for” personal information from AOL users.
Then in the early 2000s, phishers started targeting financial institutions. In 2003, customers with eBay and PayPal were hit with phishing emails requesting them to update account information, leading customers to give out log-in information.
How Does Phishing Work?
Phishers prey on their targets’ fear, curiosity, urgency, and even greed to get them to respond to their messages. Typically, phishers pose as a legitimate company to fool individuals into stealing personal information. They create emails and text messages that appear legitimate but contain dangerous links and attachments that lure their targets into taking an unknown, risky action.
Cybercriminals use phishing emails and text messages because it’s easy, cheap, and effective. That’s why thinking before you click and respond to messages is crucial, especially as these schemes become more innovative and sophisticated.
Types of Phishing Attacks
Bulk Phishing.
Build phishing is the most common phishing attack, also called deceptive phishing. Cybercriminals send fraudulent messages in bulk that make false promises: you’ve won money, qualified for a refund, or your account is delinquent, and action is required. They send the same email to many people, knowing that at least a few will become identity theft targets.
Spear Phishing.
The executors of this scheme have done their homework. To increase the cybercriminal’s chances of successfully tricking someone, they find as much personal information about their potential victim as possible. Then, they use it to craft a message that seems especially legitimate to lower the target’s guard.
Whaling Attack.
This is spear phishing, where the attacker targets a company’s executives and tries to steal their login credentials. If successful, criminals can use this sensitive information to steal from the company or impersonate the executive to scam other company employees.
Clone Phishing.
This form of phishing is particularly deceptive and can be more challenging to spot. The attacker copies the contents of a legitimate message the target has already received and replaces the original links in the message with harmful ones that lead to a fake website. To be successful, the cybercriminal will need to already have the victim’s login credentials in their possession.
Microsoft 365 Phishing.
This type of phishing tricks people into giving up their Microsoft Office 365 login information.
Business Email Compromise.
Business Email Compromise, a BEC scam, targets companies to get them to send money or reveal confidential company information.
Social Media Phishing.
This phishing scheme involves taking over a target’s social media account and stealing personal data.
Voice Phishing.
The scammer tries to impersonate legitimate companies to steal money and personal information.
Malicious Web Links.
Phishers create these links to get targets to download ransomware which can lead to spear phishing emails and other cybercrimes.
Malicious Attachments.
Cybercriminals use malicious email attachments to attack a person’s computer and steal information.
How Can I Detect Phishing?
Though cybercriminals will go to great lengths to make a message look authentic and official, many phishing emails share qualities that can be detected. Here are common features of phishing emails that you can detect.
Spelling & grammatical errors.
This is the most common way to tell if you have received a fraudulent message. Rarely will institutions or companies, especially banks, send you a poorly written email with spelling or grammar errors.
The message requests personal information.
Any email requesting login credentials or personally identifiable information should be verified directly with the organization.
The message is extremely time-sensitive.
If you’ve received a message out of the blue that offers a deal, but only if you act now, it’s probably a scam. Especially if the message threatens to close your account, err on caution by calling the institution for verification.
The offer is too good to be true.
The age-old saying applies as much here as anywhere else. Emails claiming that you’ve won just about anything or that you’re being refunded for a purchase you never made are bad news. Ignore these.
Sender’s email seems suspicious.
Slight variations in the email address that attempt to look authentic but don’t quite hit the mark are common. For example, you may bank with an institution that usually emails you from “[email protected],” but you receive an unexpected email from “[email protected].”
They may also try to alter one letter or character in the email address in hopes that the target won’t notice.
Unexpected attachment.
If you receive an email from an unknown sender that comes with an attachment you weren’t expecting, don’t click or download it. There’s a possibility that a scammer has sent you a malware or ransomware attack: to steal your information or take control of your machine.
Hyperlinks from an unknown sender.
Malicious links can be easily disguised with text that makes them appear harmless. Hover your cursor over the link to see where it leads, and if you’re unable to do so, don’t click it—take steps to verify its authenticity.
Something’s just not right.
Trust your instincts. If you receive an email and something doesn’t feel right, there’s a good chance you’re correct. Of course, it never hurts to verify authenticity, but ignoring your initial hunch and treating the email as a legitimate one can hurt.
Popular Phishing Examples
1. This email from ‘Amazon’ is filled with red flags
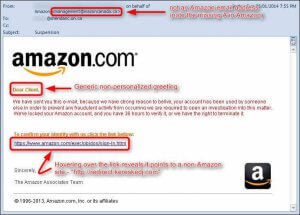
The sender has a noticeably strange email address, one of the common phishing features mentioned above.
It doesn’t appear to be official, the message is poorly written and includes a grammatical error, it tries to play on the recipients fear and call them to action, and it has a misleading link that takes the user to a different location than the text implies.
2. This Netflix phishing scam is a common trick
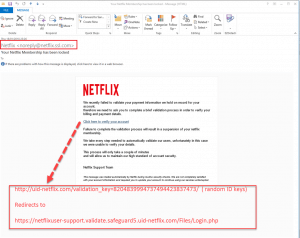
This scammer has done a decent job of crafting a convincing email, but the sender’s address seems suspicious and the link in the message is a huge red flag, another common feature listed above.
It’s never a bad idea to go straight to a website and navigate through your browser instead of clicking an email link.
3. SMS text message examples of phishing attempts
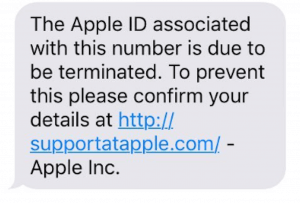
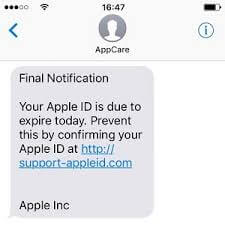
Here, the sender tries to make it appear as though the recipient has received an automatic alert from Apple regarding their iCloud account:
The links are the first indication that these messages are fraudulent. They don’t direct the user to the official Apple website.
Secondly, Apple doesn’t send text messages asking for login credential confirmations. It’s best to ignore messages like these and block the number—call Apple instead.
Where it Happens
Phishing attacks can happen at home and while you’re at work. Here are some consequences you can face when falling for a phishing attack in your personal and work life.
In Your Personal Life
- Get hold of your bank information and steal your money.
- Make unauthorized purchases with your credit card.
- File tax returns in your name.
- Commit loan fraud.
- Lose access to photos, videos, files, and other vital documents.
- Take over your social media account and create scam-like posts.
- Commit wire transfer fraud.
- Ransomware to extort money from victims.
In Your Work Life
- Exposed personal information of customers and co-workers.
- Expose sensitive communications, files, and systems.
- Damage your company’s reputation.
- Reduced investor confidence.
- Negatively impacts on your company’s revenue.
Lastly, if you work from home or consider a remote employee, understand that you can still be a target for a phisher.
Tips to Help Prevent Phishing Attacks:
Monitor your accounts regularly.
The best way to spot any suspicious activity is to actively monitor your bank account, credit, and social media accounts. If you need help with account monitoring, consider signing up for identity theft protection.
Monitoring services, like IdentityIQ, can help watch out for any suspicious activity from your credit to your social media and send you real-time alerts so you can quickly resolve it.
Keep your browser updated.
You want to keep your browser updated because it keeps your computer safe from phishing attacks, identity theft, and malware.
Don’t click on strange attachments or links.
Always be cautious when you receive an email with links and attachments, which usually contain malware.
Be aware of pop-up windows.
While pop-up windows are annoying, they can infect your computer with malware. So, be careful when clicking on a pop-up.
Never give out personal information.
Emails are typically not secure, so when you give out your personal information through email, you put yourself at risk for identity theft.
Stay on top of the latest phishing attacks.
It’s always a good idea to stay on top of the latest online scams so you better protect yourself. Consider checking the Federal Trade Commission’s website.
What Should I do If I Receive a Phishing Email?
If you find that you have received a strange email, the first step is not to open the email. Secondly, if you receive this email at work, consider contacting your IT team. They will know how to deal with spam emails. Furthermore, failing to report a phishing email can put you and your company at risk.
What to Do If You’ve Fallen Victim
If you’ve recently received and/or clicked on a suspicious email message, you can report it to the Anti-Phishing Working Group (APWG) at [email protected].
Also, you can report a phishing incident to the Federal Trade Commission at ReportFraud.ftc.gov.

